Introduction to Zero Trust Architecture
Zero Trust Architecture is a security model that operates on the fundamental principle of “never trust, always verify.” This concept assumes that threats can come from anywhere, either outside or inside the network, and hence, no user or device should be implicitly trusted.
The term “Zero Trust” was coined by John Kindervag, a principal analyst at Forrester Research, in 2010. It emerged as a response to the realization that traditional perimeter-based security models, which assume that everything within the network is trustworthy, were no longer effective in a world where security breaches were increasingly happening from within the network.
In the Zero Trust Architecture, trust is considered a vulnerability. Instead of assuming everything “inside” a network can be trusted, this model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request comes from or what resource it accesses, Zero Trust teaches us to “never trust, always verify” ─ every access request has to be fully authenticated, authorized, and encrypted before granting access.
By adopting a strategy that trusts no one, organizations can ensure that every entity, be it a user, device, application, or packet of data, is authenticated and verified before the network grants access. This approach significantly minimizes the risk of unauthorized access and protects the network from potential inside and outside threats.

Description of the Traditional Security Model
The traditional security model, also known as the perimeter-based security model or castle-and-moat approach, assumes that everything inside the network is trustworthy and everything outside the network is not. This model focuses on building strong defenses around the network to keep potential threats out.
While the traditional model has been effective in the past, it has significant shortcomings in the modern digital landscape. The rise of cloud computing, remote work, and BYOD (Bring Your Own Device) policies have blurred the network perimeter, making it difficult to distinguish between internal and external threats. Moreover, this model fails to account for threats that originate from within the network, such as insider threats or threats that arise from compromised internal devices.
Differentiation between Zero Trust Architecture and Zero Trust Network Access
Zero Trust Architecture (ZTA) and Zero Trust Network Access (ZTNA) are two concepts that stem from the Zero Trust security model, which operates on the principle of “never trust, always verify”. While both concepts share the same foundational philosophy, they focus on different aspects of network security.
ZTA is a holistic approach to network security that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network’s perimeter. It encompasses all aspects of network security, including user authentication, device authentication, micro-segmentation, and more.
On the other hand, ZTNA is a more focused concept that primarily addresses secure access. ZTNA solutions, also known as Software-Defined Perimeters (SDP), provide secure access to private applications without exposing the network to the internet. This approach reduces the attack surface by hiding network resources from the internet, making them invisible to unauthorized users.
Key Principles of Zero Trust Architecture
- Explicit Verification: The backbone of Zero Trust Architecture is the principle that every user and device must be authenticated and verified. This is to ensure that the identity of each user is validated before launching any digital interaction. The Zero Trust model operates under the belief of “never trust, always verify”. This means regardless of whether the user or device is attempting to access the network from inside or outside, verification is mandatory. This approach minimizes the risk of unauthorized access and helps protect the network from potential security threats.
- Least Privilege Access: The underlying principle of least privilege access in Zero Trust Architecture is that users and devices should only be given the bare minimum access necessary to perform their tasks. This means that if a user or device doesn’t need access to a certain resource, they won’t get it. The primary reason for this is to limit potential security exposures. If a user’s account or device is compromised, the damage that can be done is limited because the attacker can only access a minimal amount of information.
- Micro-Segmentation: Micro-segmentation is a key aspect of Zero Trust Architecture that enhances security. It involves dividing the network into smaller, more manageable segments or zones. Each of these segments is isolated and has its own unique security controls. This means if an attacker manages to penetrate one segment, they are prevented from moving laterally across the entire network. This compartmentalization of the network significantly reduces the attack surface and helps prevent the spread of threats.
- Continuous Monitoring: Continuous monitoring is another crucial principle of Zero Trust Architecture. With the ever-evolving nature of security threats, it’s essential to constantly monitor all network activities to detect any anomalies or suspicious behavior promptly. Continuous monitoring in Zero Trust not only helps in real-time threat detection but also aids in the swift response to potential security incidents. It provides the ability to analyze and learn from past incidents to improve future security measures.
- Encryption: Encryption plays a pivotal role in the Zero Trust Architecture by providing an additional layer of security. It involves converting data into a code to prevent unauthorized access. Even if an attacker manages to breach the network defenses, the encrypted data they find will be useless without the correct decryption keys. In a Zero Trust Architecture, data is encrypted at all stages – at rest, in transit, and in use. This ensures that sensitive data remains secure, further fortifying the network against potential breaches.

Benefits and Challenges of Zero Trust Architecture
Benefits:
- Improved Security: The most notable advantage of Zero Trust Architecture is enhanced security. This model operates on the principle of “never trust, always verify,” which significantly reduces the likelihood of unauthorized access and potential security threats.
- Reduced Risk of Data Breaches: By implementing the least privilege access, the risk of data breaches is significantly reduced. If a user’s account or device is compromised, the breach is contained to a minimal amount of information, preventing widespread data exposure.
- Better Control Over Access to Resources: With explicit verification and micro-segmentation, organizations have more granular control over who and what has access to specific resources. This precise control helps to further secure sensitive data and critical systems.
Challenges
- Need for Significant Infrastructure Changes: Transitioning to a Zero Trust Architecture often requires substantial changes to an organization’s existing infrastructure. This can involve reconfiguring network designs, implementing new security controls, and updating policies.
- Complexity of Implementation: The implementation of Zero Trust Architecture can be complex and time-consuming. It requires a deep understanding of the organization’s network, resources, and user behaviors, as well as the ability to effectively deploy and manage advanced security solutions.
- Potential Resistance from Users: The stringent access controls and continuous verification processes in Zero Trust Architecture can lead to resistance from users, especially if they find the new measures inconvenient or intrusive. It’s crucial for organizations to balance security and usability, and to educate users about the importance of these measures for their own protection and the protection of the organization.
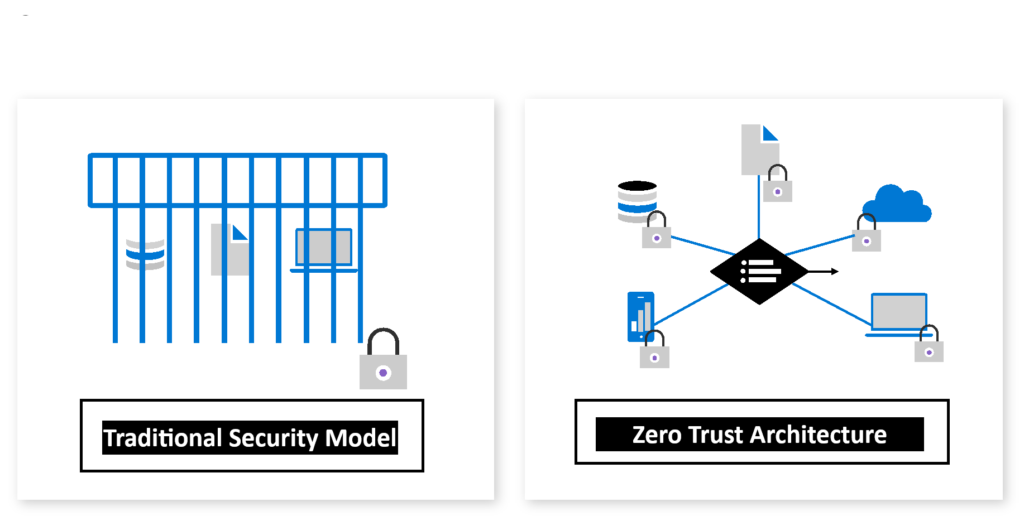
Transitioning from a traditional security model to a Zero Trust model
Here are the steps to transition from a traditional security model to a Zero Trust model:
- Understand Your Network: The first step involves gaining a complete understanding of your network, including data flows and dependencies. This helps identify the assets that need protection.
- Map Transaction Flows: The second step involves mapping the transaction flows of all applications and data, including understanding how data moves across your network.
- Build a Zero Trust Architecture: Once you have a clear understanding of your network, the next step is to build a Zero Trust Architecture that includes a single, strong user and device authentication.
- Monitor and Manage: After implementing the Zero Trust Architecture, continuous monitoring and managing is necessary to ensure its effectiveness.
Role of Technologies in Zero Trust Architecture:
- Multi-Factor Authentication (MFA): MFA is an essential aspect of Zero Trust Architecture. It adds an additional layer of security by requiring more than one form of authentication from independent categories of credentials.
- Identity and Access Management (IAM): IAM is a framework of policies and technologies ensuring that the right people have access to the right resources at the right times for the right reasons. It plays a pivotal role in verifying and managing user identities and their access rights.
- Security Information and Event Management (SIEM): SIEM solutions collect and aggregate log data generated throughout the organization’s technology infrastructure, identify deviations from the norm, and take appropriate action.
Case Studies of Zero Trust Architecture Implementation
Google’s BeyondCorp
Google’s implementation of Zero Trust Architecture, known as BeyondCorp, shifts access controls from the network perimeter to individual users and devices. This model allows Google’s employees to work securely from any location without needing a traditional VPN.
In traditional security models, anything within the network’s perimeter is trusted. However, BeyondCorp eliminates the concept of trust based on network location. It builds upon technologies such as single sign-on and multi-factor authentication, combined with a device inventory database and a policy enforcement engine.
Google’s approach verifies the user and the device, then combines this information with the user’s responsibilities and tasks to decide whether access should be granted or not. Hence, instead of securing the perimeter, BeyondCorp focuses on securing the data by continuously assessing the trustworthiness of interactions between users and data.
IBM’s Zero Trust Model
IBM’s approach to Zero Trust is based on the principle of ‘never trust, always verify’. They have implemented a model that establishes user trust based on device and user credentials, resulting in a more secure environment.
IBM’s Zero Trust strategy is heavily reliant on AI to detect anomalies in user behavior. They use their own AI tool, Watson, in combination with their Security Information and Event Management (SIEM) system. The AI capabilities of Watson allow IBM to analyze vast amounts of security data, identify potential threats, and react to them much faster.
Furthermore, IBM uses Identity and Access Management (IAM) solutions to ensure that the right users have the right access for the right reasons. By integrating IAM with AI, IBM can continuously evaluate and align access privileges based on changing user roles and profiles, thereby significantly reducing the risk of insider threats.
Both Google’s and IBM’s implementations highlight the effectiveness of the Zero Trust Architecture in enhancing an organization’s security posture by reducing the attack surface and improving the ability to respond to potential threats.

Conclusion
In this era of increasing cyber threats, Zero Trust Architecture acts as an effective security model, providing a robust defense against potential intrusions. By operating on the principle of “never trust, always verify,” it ensures that every user, device, or data packet is authenticated and authorized before gaining access to network resources.
The key principles of Zero Trust Architecture – explicit verification, least privilege access, micro-segmentation, continuous monitoring, and encryption – combine to create a strong and dynamic security framework. This model provides numerous benefits, including improved security, reduced risk of data breaches, and better control over access to resources. However, the transition to this architecture also presents certain challenges, such as the need for significant infrastructure changes, the complexity of implementation, and the potential resistance from users.
Technologies such as Multi-Factor Authentication, Identity and Access Management, and Security Information and Event Management play a crucial role in executing a successful Zero Trust strategy. Notable examples of Zero Trust implementation, like Google’s BeyondCorp and IBM’s Zero Trust Model, highlight the effectiveness of this architecture in enhancing organizational security.
As we wrap up this comprehensive guide on Zero Trust Architecture, it calls for organizations to consider implementing this security model in their own networks. In the face of growing cyber threats, the need for robust and dynamic security measures like Zero Trust Architecture has never been more critical. It’s time for organizations to shift their mindset from the traditional “trust but verify” approach to a more proactive “never trust, always verify” stance. As we move forward in the digital age, let’s strive to create a safer, more secure cyber environment for all.